Chipmaker Qualcomm warns of three actively exploited zero-days
Security Affairs
OCTOBER 4, 2023
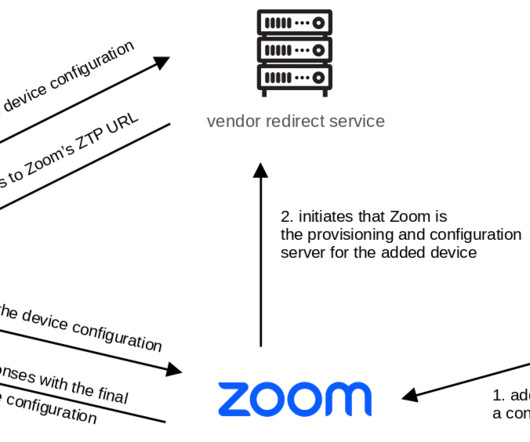
Google Threat Analysis Group and Google Project Zero first reported that the CVE-2023-33106, CVE-2023-33107, CVE-2022-22071 and CVE-2023-33063 are actively exploited in targeted attacks. “CVE-2022-22071 was included in our May 2022 public bulletin. CVE-2023-28540 : Improper Authentication in Data Modem.










































Let's personalize your content