Experts share details of five flaws that can be chained to hack Netgear RAX30 Routers
Security Affairs
MAY 11, 2023
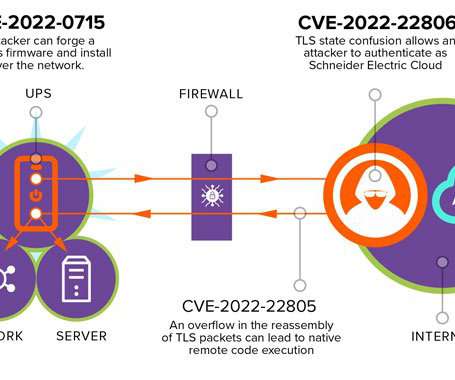
“Successful exploits could allow attackers to monitor users’ internet activity, highjack internet connections and redirect traffic to malicious websites or inject malware into network traffic. “NETGEAR strongly recommends that you download the latest firmware as soon as possible.” We are in the final!









































Let's personalize your content