GoTo revealed that threat actors stole customers’ backups and encryption key for some of them
Security Affairs
JANUARY 24, 2023
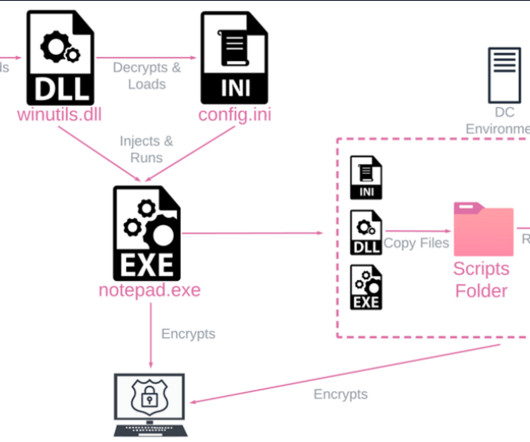
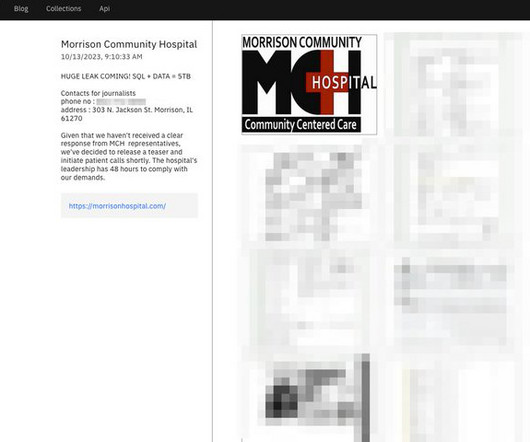
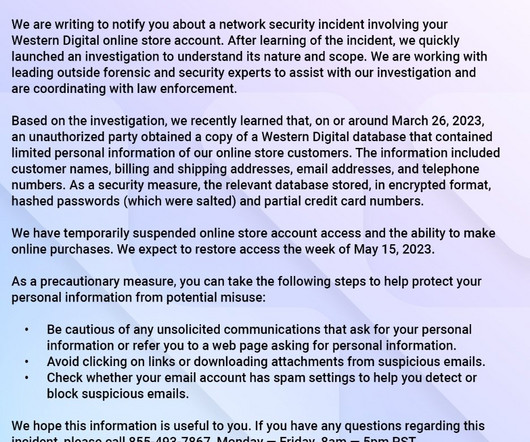
GoTo is notifying customers that its development environment was breached in November 2022, attackers stole customers’ backups and encryption key. The security breach was disclosed in November 2022, but at the time the company was not able to determine the impact on its customers’ data.









































Let's personalize your content