A Day in the Life of a Prolific Voice Phishing Crew
Krebs on Security
JANUARY 7, 2025
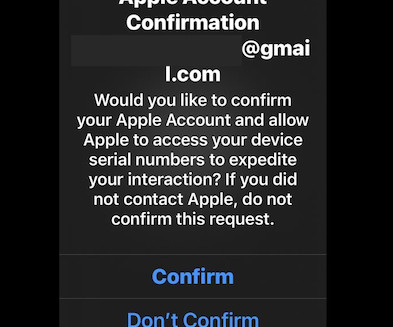
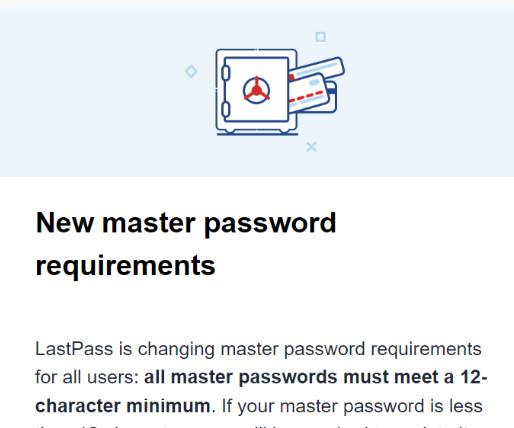
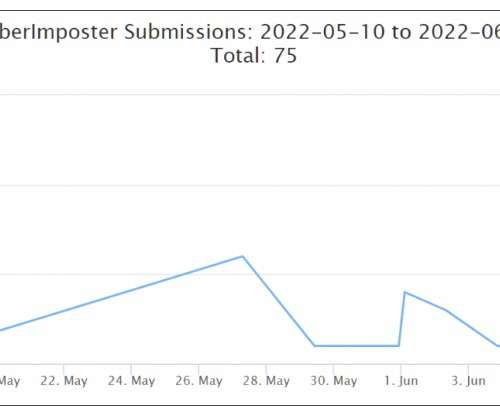
AUTODOXERS According to Stotle, the target lists used by their phishing callers originate mostly from a few crypto-related data breaches, including the 2022 and 2024 breaches involving user account data stolen from cryptocurrency hardware wallet vendor Trezor. com and two other related control domains — thebackendserver[.]com






























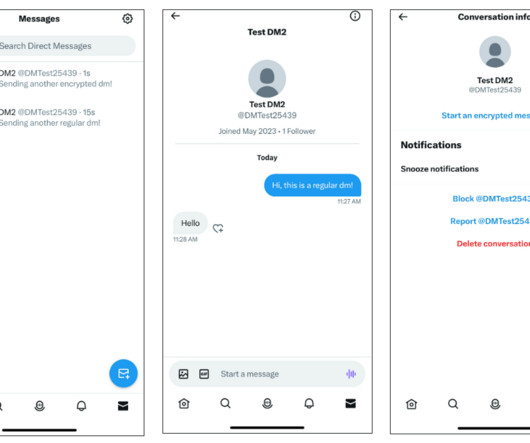


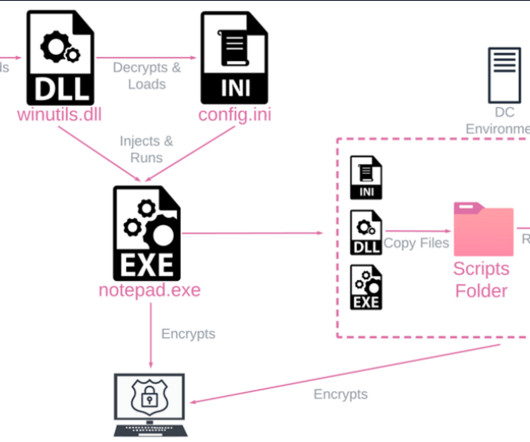













Let's personalize your content