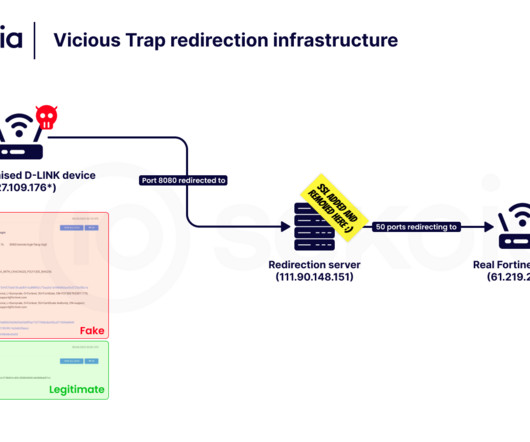
ViciousTrap: New Cyber-Espionage Group Hijacks Routers for Honeypot Surveillance
Penetration Testing
MAY 24, 2025
Sekoia.ios Threat Detection & Research (TDR) team has unveiled a novel adversary, dubbed “ViciousTrap”, that hijacks compromised SOHO The post ViciousTrap: New Cyber-Espionage Group Hijacks Routers for Honeypot Surveillance appeared first on Daily CyberSecurity.












































Let's personalize your content