Experts spotted a variant of the Agenda Ransomware written in Rust
Security Affairs
DECEMBER 19, 2022
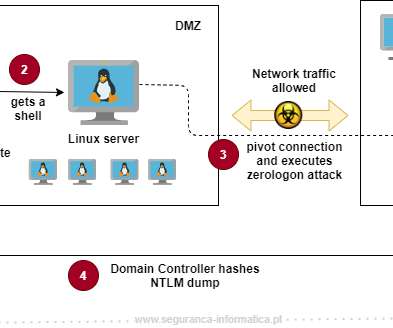
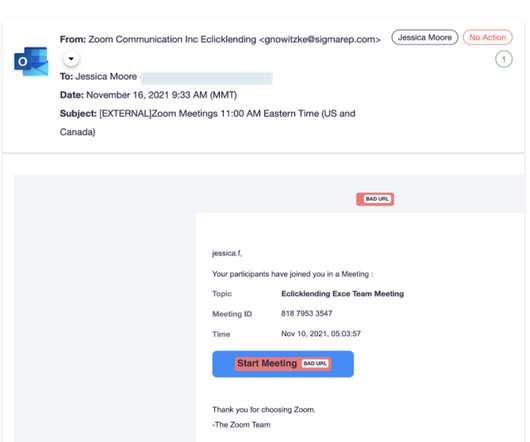
The main reasons to rewrite malware in Rust is to have lower AV detection rates, compared to malware written in most common languages, and to target multiple architectures. The Rust variant has also been seen using intermittent encryption, one of the emerging tactics that threat actors use today for faster encryption and detection evasion.”













































Let's personalize your content