Is Artificial Intelligence Making People More Secure? Or Less?
Security Boulevard
JULY 20, 2023
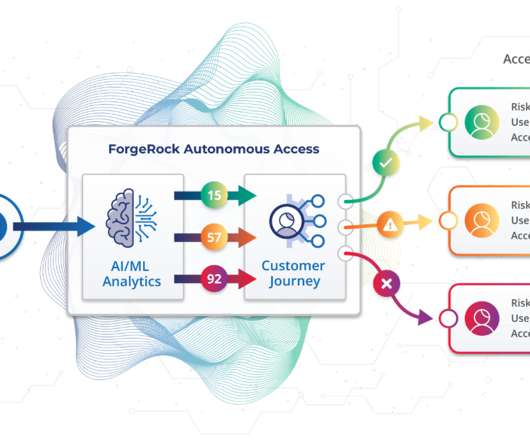
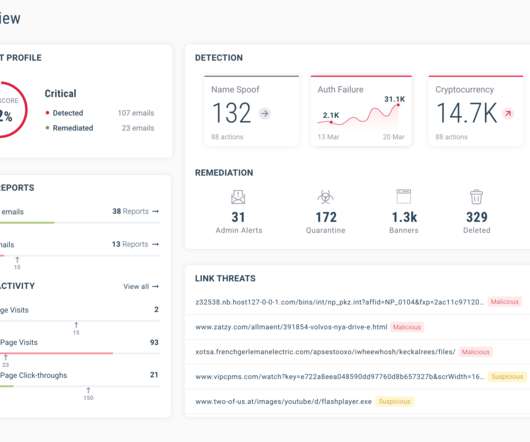
AI can be used to monitor user behavior and make real-time decisions about whether to grant access or add step-up authentication if there is anything anomalous about the request (such as a login from an unusual timezone). If it detects a threat or anomalous behavior, its dashboard explains the decision in human-readable form.
















































Let's personalize your content