Passwordless Authentication without Secrets!
Thales Cloud Protection & Licensing
OCTOBER 11, 2024
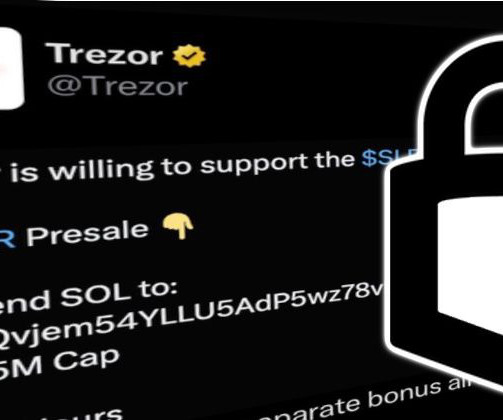
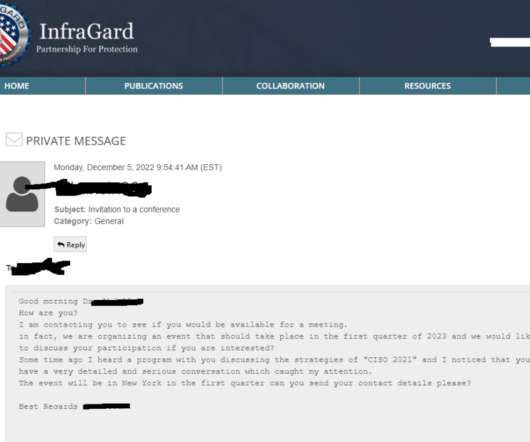
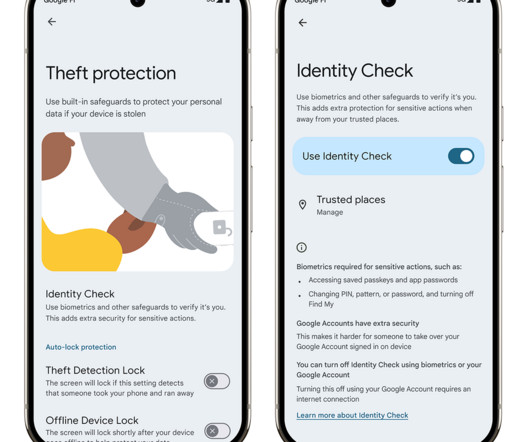
Passwordless Authentication without Secrets! This highlights an increasing demand for advanced authentication methods like passkeys and multi-factor authentication (MFA), which provide robust security for most use cases. Similarly, in retail and manufacturing, delays caused by authentication procedures reduce overall efficiency.












































Let's personalize your content