Ransomware: Why do backups fail when you need them most?
Malwarebytes
OCTOBER 22, 2021
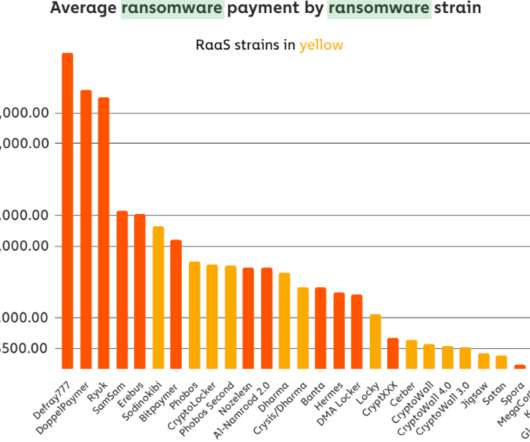
It’s widely known, and endlessly repeated, that the last, best line of defence against the potentially devastating effects of a ransomware attack is your backups. Ski Kacoroski, System administrator, Northshore School District. Why do backups fail? This is what we learned from Crape: Backups are difficult.





























Let's personalize your content