Social Media Account Verification Messages: CyberCriminals’ Latest Phishing Technique Exploits Both Human Emotions And Anti-Fraud Techniques
Joseph Steinberg
DECEMBER 1, 2020
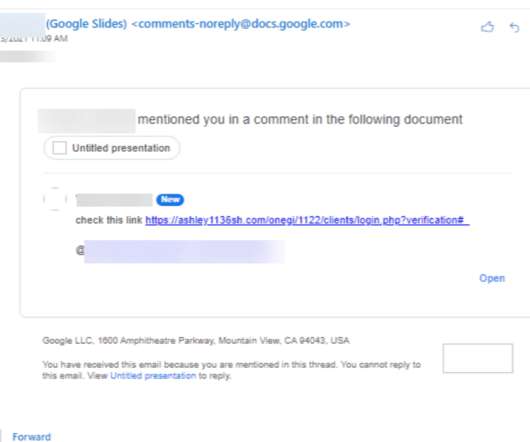
Social media users’ delight at receiving notification that their accounts have qualified for Verification (that is, receiving the often-coveted “blue check mark” that appears on the social media profiles of public figures) has become the latest target of criminal exploitation.







































Let's personalize your content