A large botnet targets M365 accounts with password spraying attacks
Security Affairs
FEBRUARY 24, 2025
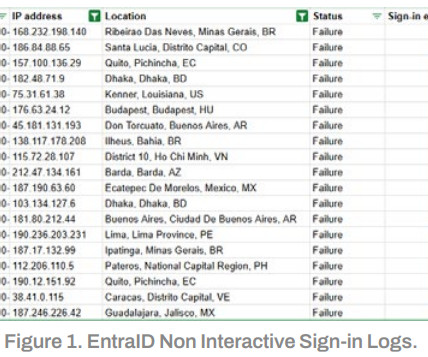
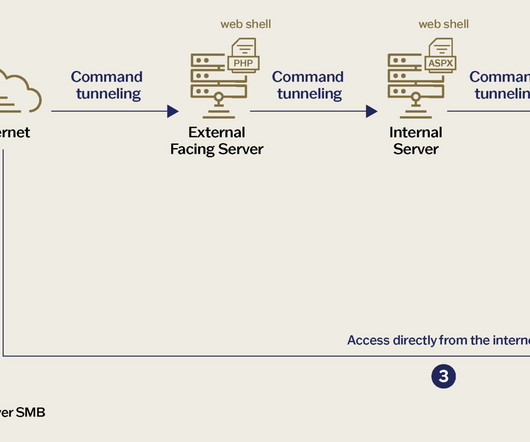
A botnet of 130,000+ devices is attacking Microsoft 365 accounts via password-spraying, bypassing MFA by exploiting basic authentication. SecurityScorecard researchers discovered a botnet of over 130,000 devices that is conducting password-spray attacks against Microsoft 365 (M365) accounts worldwide. ” continues the report.










































Let's personalize your content