Ransomware Group Turns to Facebook Ads
Krebs on Security
NOVEMBER 10, 2020
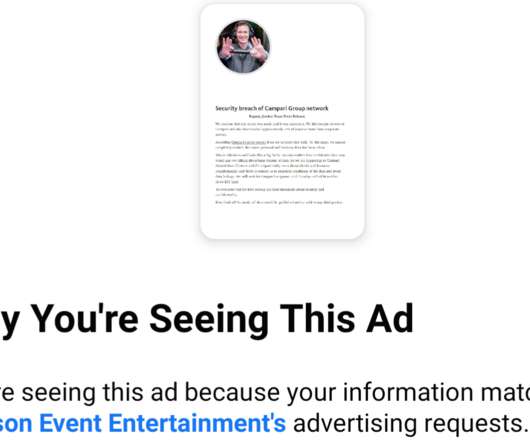
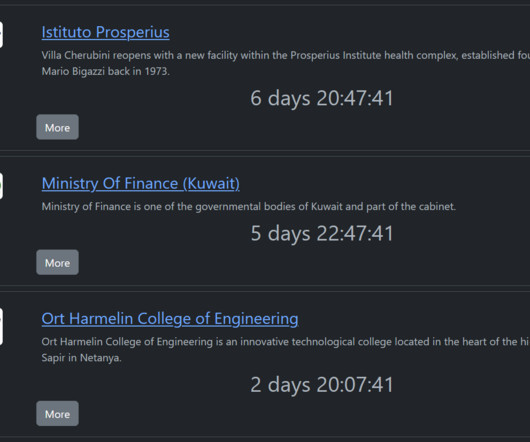
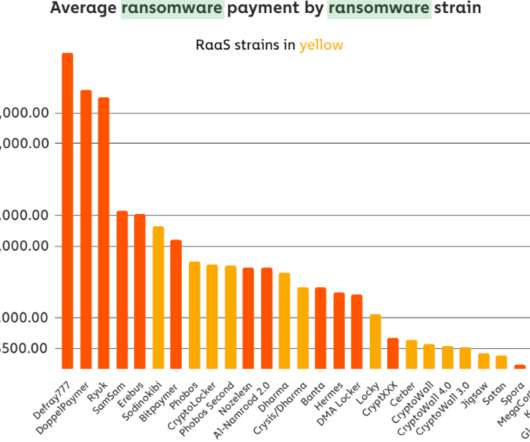
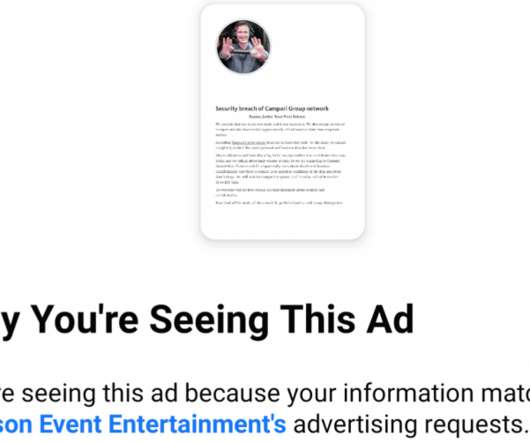
It’s bad enough that many ransomware gangs now have blogs where they publish data stolen from companies that refuse to make an extortion payment. Now, one crime group has started using hacked Facebook accounts to run ads publicly pressuring their ransomware victims into paying up. On the evening of Monday, Nov. ”











































Let's personalize your content