Google asks users to be aware of Phishing Attacks on Google Drive
CyberSecurity Insiders
JUNE 21, 2021
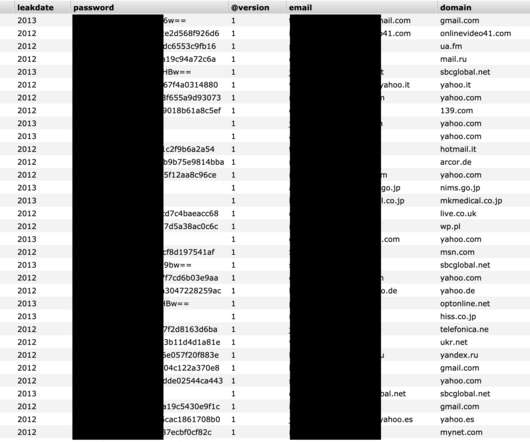
In what is known to our Cybersecurity Insiders, hackers are seen launching phishing campaigns against Google Drive users by sending them email’s filled with malicious links and locking them from their accounts thereafter. In the year 2019, Trend Micro detected over 61.2 billion cyber threats targeting online users via emails.













































Let's personalize your content