Calendar Meeting Links Used to Spread Mac Malware
Krebs on Security
FEBRUARY 28, 2024
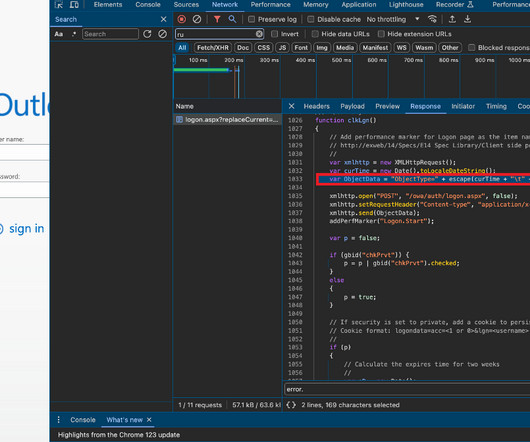
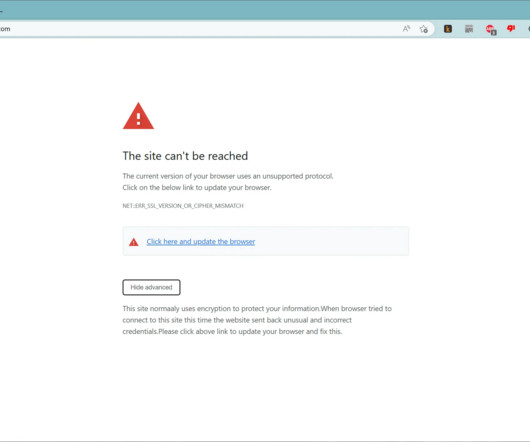
But clicking the meeting link provided by the scammers prompts the user to run a script that quietly installs malware on macOS systems. The profile also linked to Mr. Lee’s Twitter/X account , which features the same profile image. “Some of our users are facing issues with our service,” the message read.




































Let's personalize your content