News alert: SquareX discloses nasty browser-native ransomware that’s undetectable by antivirus
The Last Watchdog
MARCH 28, 2025
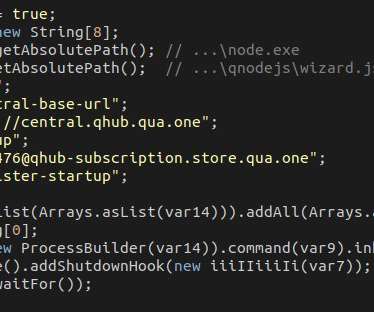
Ransomware attacks typically involve tricking victims into downloading and installing the ransomware, which copies, encrypts, and/or deletes critical data on the device, only to be restored upon the ransom payment. Traditionally, the primary target of ransomware has been the victims device. .














































Let's personalize your content