Latin American Javali trojan weaponizing Avira antivirus legitimate injector to implant malware
Security Affairs
FEBRUARY 16, 2021
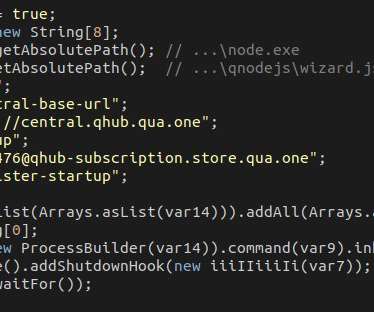
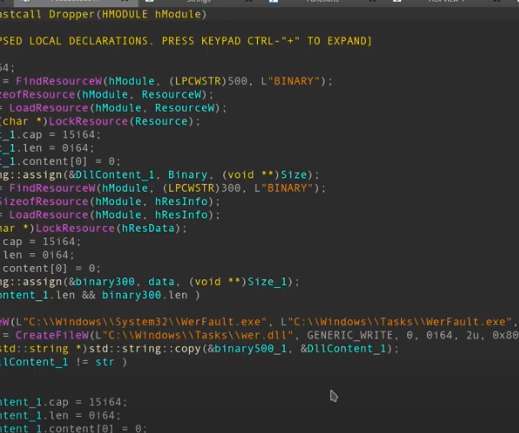
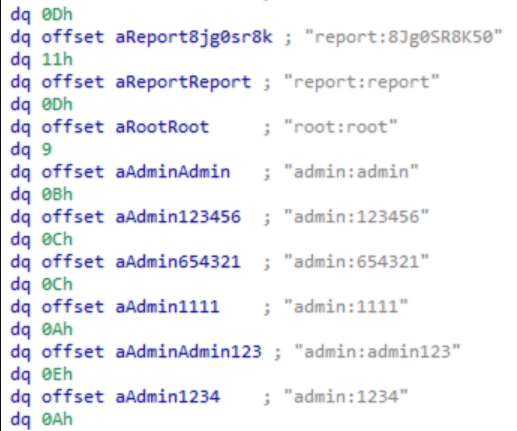
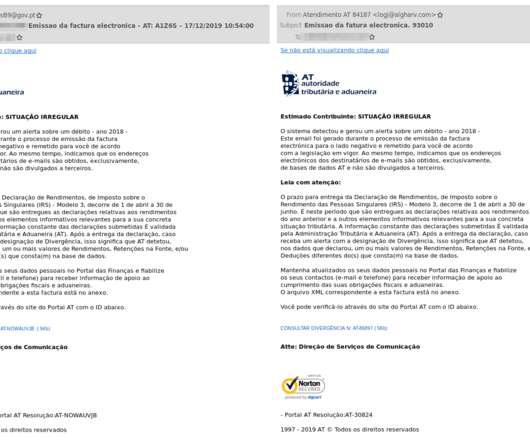
Latin American Javali trojan weaponizing Avira antivirus legitimate injector to implant malware. The initial stage of these trojans is generally the execution of a dropper in a form of a VBS, JScript, or MSI file that downloads from the Cloud (AWS, Google, etc.) the trojan loader/injector.











































Let's personalize your content