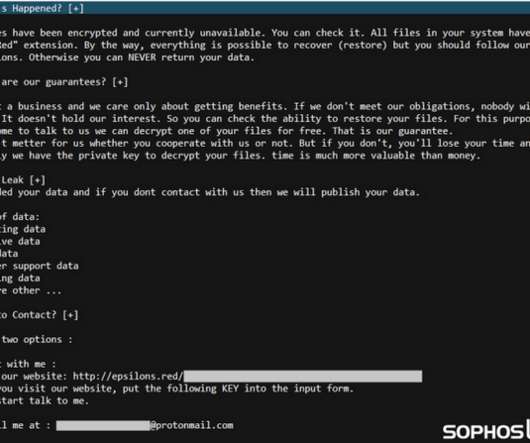
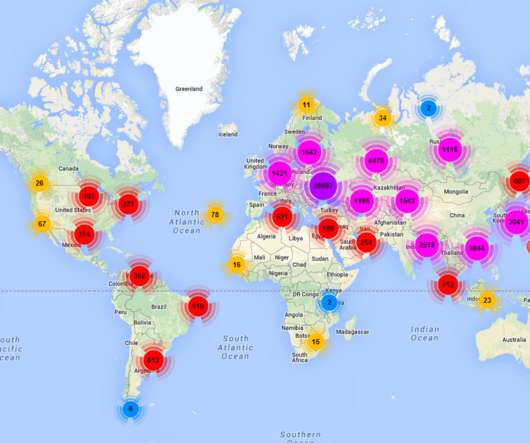
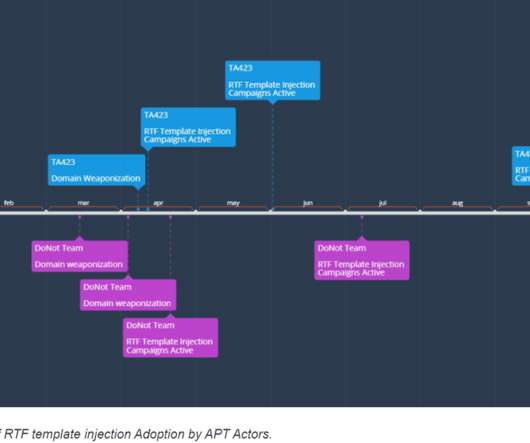
DarkRace Ransomware: A Deep Dive into its Techniques and Impact
Quick Heal Antivirus
AUGUST 18, 2023
As cyber threats continue to evolve, a new ransomware has been discovered bearing unmistakable similarities to another well-known. The post DarkRace Ransomware: A Deep Dive into its Techniques and Impact appeared first on Quick Heal Blog.
















































Let's personalize your content