New Shlayer Mac malware spreads via poisoned search engine results
Security Affairs
JUNE 21, 2020
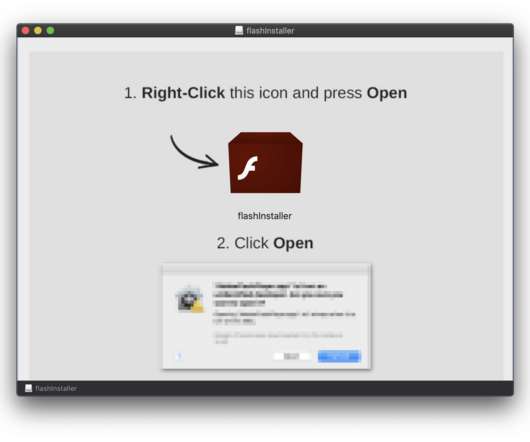
Shlayer Mac malware is back, the Mac threat is now spreading through new black SEO operations. Researchers spotted a new version of the Shlayer Mac malware that is spreading via poisoned Google search results. The malware can be used to download other malicious payloads, including malware or adware. up to 10.14.3.














































Let's personalize your content