Chinese Antivirus Firm Was Part of APT41 ‘Supply Chain’ Attack
Krebs on Security
SEPTEMBER 17, 2020
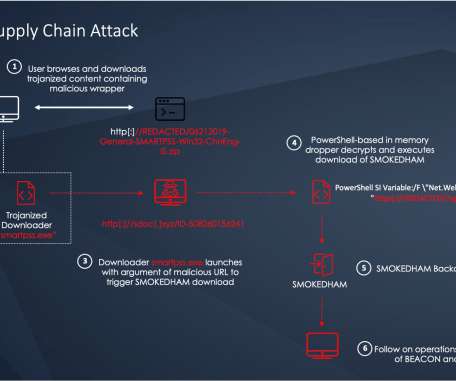
One of the alleged hackers was first profiled here in 2012 as the owner of a Chinese antivirus firm. APT41’s activities span from the mid-2000s to the present day. When I first scanned Anvisoft at Virustotal.com back in 2012, none of the antivirus products detected it as suspicious or malicious. Image: FBI.

















































Let's personalize your content