Data Centric Zero Trust for Federal Government Cybersecurity
McAfee
AUGUST 11, 2021
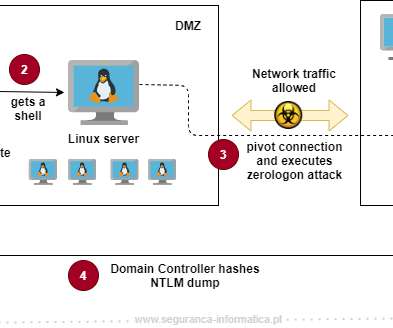
As outlined in Executive Order on Improving the Nation’s Cybersecurity (EO 14028), Section 3: Modernizing Federal Government Cybersecurity, CISA has been tasked with developing a Federal cloud-security strategy to aid agencies in the adoption of a Zero Trust Architecture to meet the EO Requirements. Data Centric Enterprise.

















































Let's personalize your content