Hyperautomation and Cybersecurity – A Platform Approach to Telemetry Architectures
McAfee
AUGUST 3, 2021
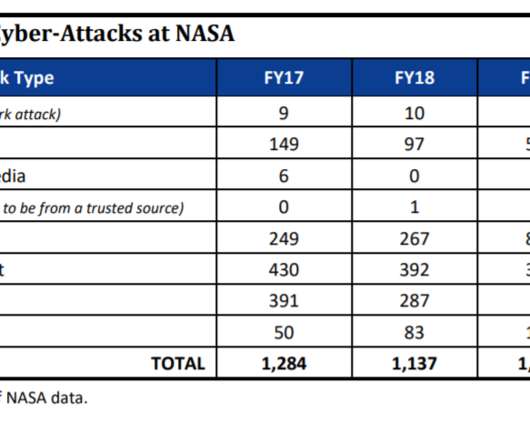
Hyperautomation is a process where artificial intelligence (AI), machine learning (ML), event-driven software, and other tools are used to automate as many business and IT processes as possible. Our target is “shift-left” security — leveraging intelligence to enhance predictability and encourage proactive responses to cyber threats.

















































Let's personalize your content