Unmasking the Cracks of Today’s Cyber Defence
Jane Frankland
OCTOBER 31, 2023
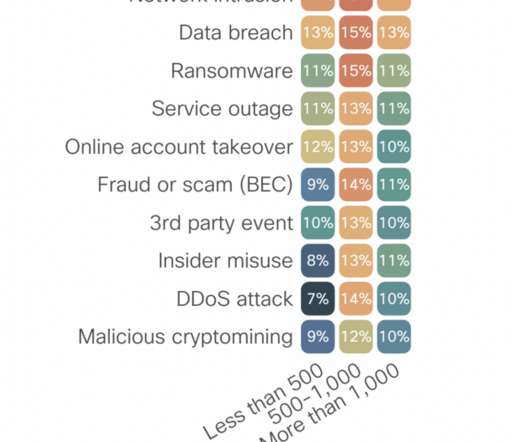
Instead, they’ve become complacent in their defence practices and may be exposing themselves to increased risks without even realising it. I’ve partnered with e2e-assure, a leading managed threat detection and response firm as I believe in their brand. You know about tech complexities and optimisation.


















































Let's personalize your content