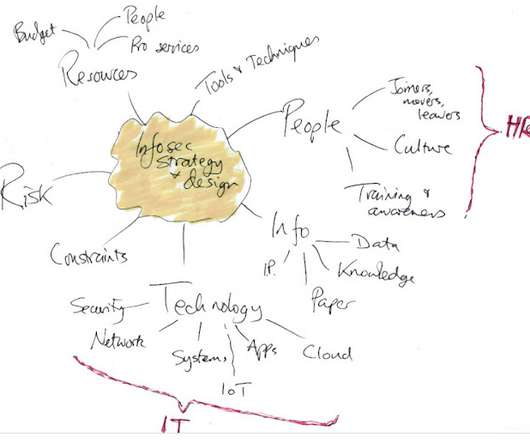
The business case for security strategy and architecture
Notice Bored
AUGUST 8, 2022
c omplementing and supporting various other business strategies and architectures such as cloud first, artificial intelligence, IIoT, big data, new products, new markets.); Defining a coherent sequence or matrix of strategic initiatives (projects, investments, business and technology changes.) Bringing clarity and direction (focus!)











































Let's personalize your content