Cybersecurity Research Topics for Beginners: Exploring the Fundamentals
CyberSecurity Insiders
MAY 28, 2023
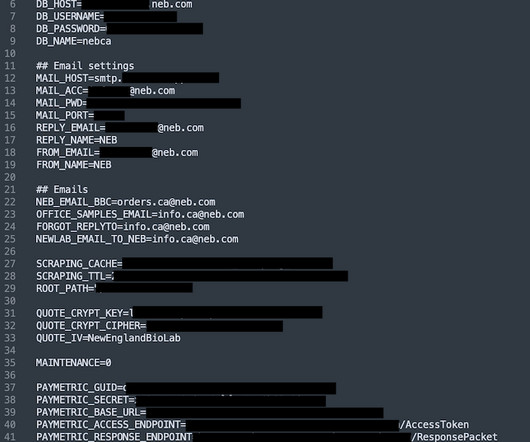
Cryptography: Dive into the world of cryptography, studying symmetric and asymmetric encryption, digital signatures, and cryptographic algorithms. Explore topics like key management, secure communication protocols, and encryption in different contexts.















































Let's personalize your content