Named Data Networking for IoT
Security Boulevard
DECEMBER 9, 2021
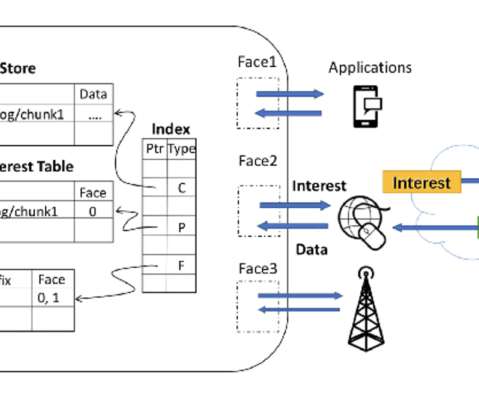
What is Named Data Networking for IoT Source: [link] The rise of the Internet of Things (IoT) has urged a new Internet architecture as IoT differs from the current Internet architecture due to constraints of devices’ resources and enormous volumes of small exchanged data.

















































Let's personalize your content