Building a Ransomware Resilient Architecture
eSecurity Planet
DECEMBER 2, 2022
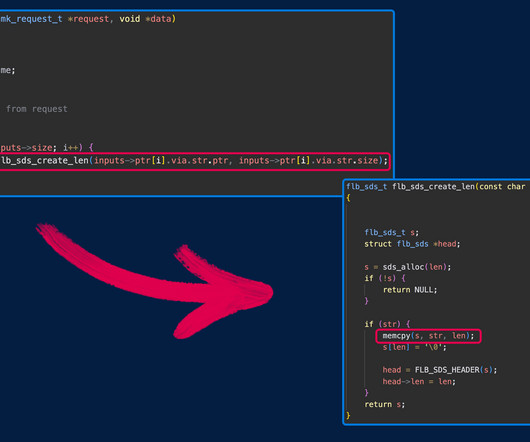
While security teams layer essential preventative measures, resilience measures also need to be implemented in an architecture to reduce the impact of ransomware attacks on your backups. Threat actors cannot hack what they cannot see. Figure 1: Typical VLAN architecture. Figure 2: Resilient VLAN architecture.












































Let's personalize your content