Flaws in mobile Internet protocol GTP allow hackers to target 5G users
Security Affairs
JUNE 15, 2020
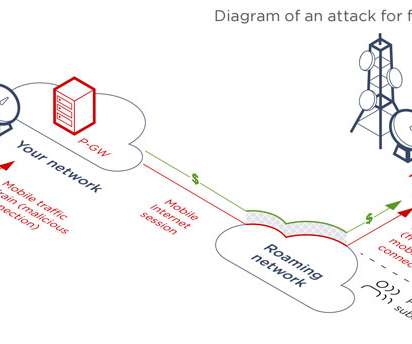
Security vulnerabilities in modern communication protocol GTP used by mobile network operators can be exploited by attackers to target 4G/5G users. “The GTP protocol contains a number of vulnerabilities threatening both mobile operators and their clients. Every network tested was vulnerable to DoS, impersonation, and fraud.”














































Let's personalize your content