What is 5G security? Explaining the security benefits and vulnerabilities of 5G architecture
CyberSecurity Insiders
SEPTEMBER 21, 2021
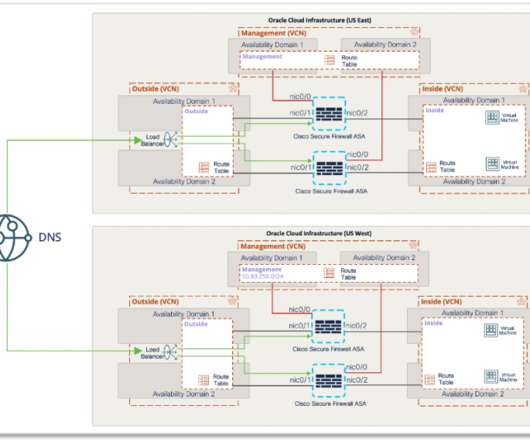
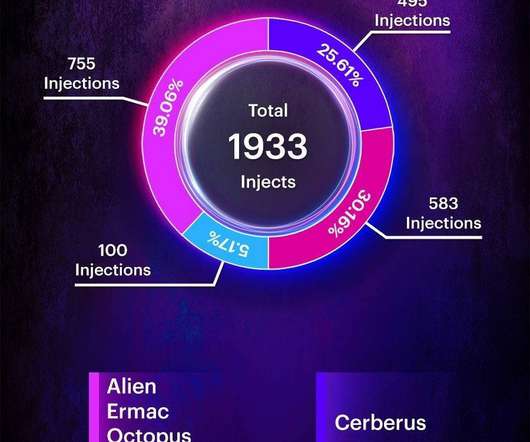
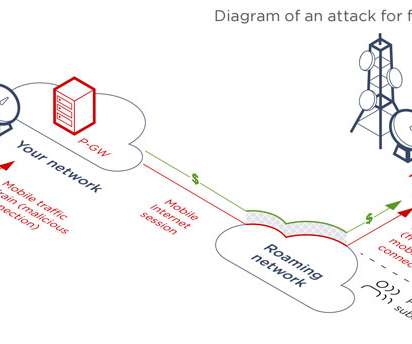
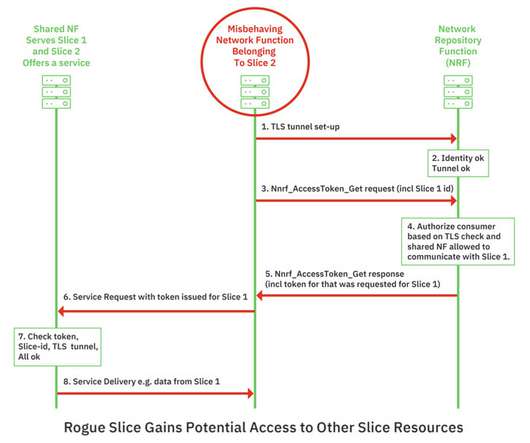
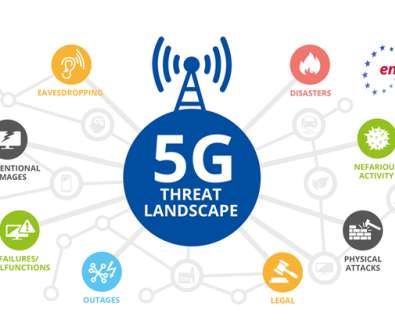
5G is already transforming and enhancing mobile connectivity. With 5G networks, billions of devices and IoT (the internet of things) are interconnectible — leading to use cases like smart cities, AR/VR on mobile networks, remote medicine and much more. Defining 5G security and architecture. What risks does 5G introduce?








































Let's personalize your content