Sunsetting legacy Cybersecurity Process for Better Optimization and Security Modernization
Security Boulevard
SEPTEMBER 19, 2022
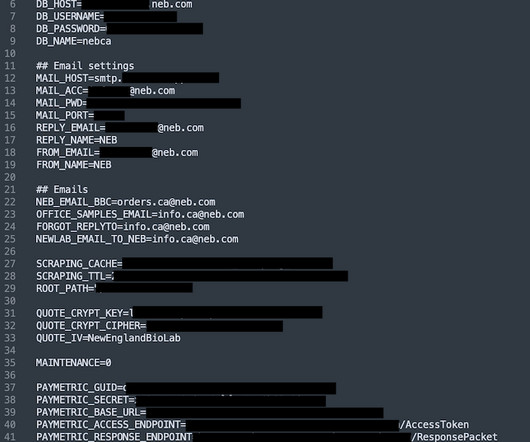
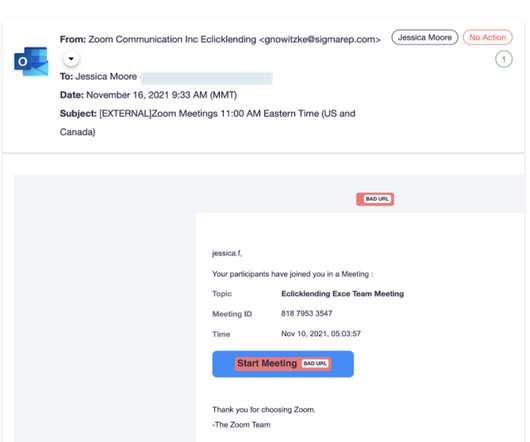
The cost of sunsetting security products, legacy applications, and legacy technology imposes a financial strain on every organization. Before considering sunsetting technology products, most SecOps and DevOps teams focus on evaluating and updating, if possible, legacy processes, including developing a legacy-system modernization workflow.
















































Let's personalize your content