Cisco Confirms Data Breach, Hacked Files Leaked
Dark Reading
AUGUST 11, 2022
Ransomware gang gained access to the company's VPN in May by convincing an employee to accept a multifactor authentication (MFA) push notification.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Dark Reading
AUGUST 11, 2022
Ransomware gang gained access to the company's VPN in May by convincing an employee to accept a multifactor authentication (MFA) push notification.

Hot for Security
MARCH 29, 2021
Have you ever wondered why your email address and other information appeared in a data breach impacting a platform you never signed up for? and River City Media data breaches. Who is Verifications.io, and what information was exposed in the data breach? Was your personal data exposed in a data breach?
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
APRIL 12, 2019
At least four VPN apps sold or made available to enterprise customers share security flaws, warns the Carnegie Mellon University CERT Coordination Center (CERT/CC). Virtual private networks (VPNs) are affordable, easy to use, and a vital component in your system. What if these VPNs are vulnerable to attackers? 8.3R6, and 9.0R2.

The Last Watchdog
MARCH 6, 2021
Set-up 2-factor authentication. If somehow passwords are leaked, a hacker can cause a data breach. Two-factor authentication or two-step verification involves adding a step to add an extra layer of protection to accounts. A two-factor verification helps in protecting from a cybersecurity breach.

Security Affairs
JULY 29, 2022
Therefore, strong authentication methods are needed. Therefore, strong authentication methods are needed to improve security without hindering user convenience. What is Strong Authentication? The IAM Security Boundary Strong authentication is a critical component of modern-day identity and access management.

eSecurity Planet
AUGUST 27, 2024
A virtual private network (VPN) does more than just mask your identity—it fundamentally changes how your data moves across the internet. But what’s really going on under the hood when you browse the web using a VPN? This encrypted data is nearly impossible to intercept and read without the appropriate decryption key.

Webroot
MARCH 3, 2025
The growing risks to your data During the third quarter of 2024, data breaches exposed more than 422 million records worldwide. As of 2024, the average cost of a data breach in the United States amounted to $9.36 In comparison, the global average cost per data breach was $4.88

Krebs on Security
MAY 19, 2020
In January 2019, dozens of media outlets raised the alarm about a new “megabreach” involving the release of some 773 million stolen usernames and passwords that was breathlessly labeled “the largest collection of stolen data in history.” “ Sanixer “) from the Ivano-Frankivsk region of the country.

IT Security Guru
OCTOBER 26, 2023
Enter Two-Factor Authentication, or 2FA for short. Here’s a shocking stat: according to the Verizon Data Breach Investigations Report , 81% of hacking-related breaches leverage either stolen or weak passwords. Always use VPN for your safety to protect your data from prying eyes. What Exactly is 2FA?

Zero Day
JUNE 6, 2025
Also: Massive data breach exposes 184 million passwords for Google, Microsoft, Facebook, and more Individually, any one of those pieces of data can be exploited by the wrong people. The records are being linked to the same ones compromised by cybercriminals in a data breach that AT&T announced in July of 2024.

Webroot
JUNE 17, 2025
Research shows that the travel and tourism sector ranked third in cyberattacks, with nearly 31% of hospitality organizations experiencing a data breach and a record 340 million people affected by cybercrimes. Fewer than 1 in 3 travelers (31%) protect their data with a virtual private network (VPN) when traveling internationally.

Malwarebytes
NOVEMBER 6, 2024
Lock things down Having a strict policy to protect your important assets with strong passwords and multi-factor authentication (MFA) should be a no-brainer. Use a firewall and VPN A firewall protects an entry point to a network while a VPN creates an encrypted tunnel between two networks.

Krebs on Security
OCTOBER 21, 2019
Antivirus and security giant Avast and virtual private networking (VPN) software provider NordVPN each today disclosed months-long network intrusions that — while otherwise unrelated — shared a common cause: Forgotten or unknown user accounts that granted remote access to internal systems with little more than a password.

Krebs on Security
APRIL 6, 2022
Many organizations are already struggling to combat cybersecurity threats from ransomware purveyors and state-sponsored hacking groups, both of which tend to take days or weeks to pivot from an opportunistic malware infection to a full blown data breach. “These guys were not leet , just damn persistent.”

Security Affairs
JUNE 2, 2024
Every week the best security articles from Security Affairs are free for you in your email box. Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press.

Adam Levin
FEBRUARY 7, 2019
While the personal data of 4,557 students, or 2,800 Girl Scouts , or 3,000 Minnesotans might pale in comparison to the steady flow of mega breaches from the likes of Equifax or Collection #1-5, but any of them have the ability to effectively sink a business financially.

SecureWorld News
JUNE 3, 2024
It did not contain sensitive data. The access was possible because the demo account was not behind Okta or Multi-Factor Authentication (MFA), unlike Snowflake's corporate and production systems. A better solution is to move towards passwordless authentication wherever possible. MFA as a user experience is far from perfect.

Security Affairs
NOVEMBER 3, 2024
Chinese threat actors use Quad7 botnet in password-spray attacks FBI arrested former Disney World employee for hacking computer menus and mislabeling allergy info Sophos details five years of China-linked threat actors’ activity targeting network devices worldwide PTZOptics cameras zero-days actively exploited in the wild New LightSpy spyware (..)

Krebs on Security
JULY 10, 2022
“I was able to answer the credit report questions successfully, which authenticated me to their system,” Turner said. That’s because Experian does not offer any type of multi-factor authentication options on consumer accounts. But now he’s wondering what else he could do to prevent another account compromise.

Security Affairs
FEBRUARY 16, 2024
The threat actor compromised network administrator credentials through the account of a former employee that was used to successfully authenticate to an internal virtual private network (VPN) access point. The threat actor likely obtained the employee’s account credentials from a third-party data breach.
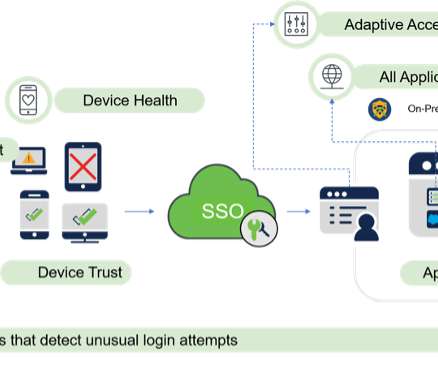
Cisco Security
AUGUST 4, 2021
Zero Trust principles help protect against identity and access-based security risks by requiring all users, whether inside or outside the organization’s network, to be authenticated, authorized, and continuously validated for security configuration and posture checks before granted access to applications and data. LinkedIn.

Security Affairs
AUGUST 12, 2024
OpenVPN is an open-source software that provides a secure and flexible way to establish a Virtual Private Network (VPN) connection. Attackers can exploit the flaws to gain full control over targeted endpoints, potentially resulting in data breaches, system compromise, and unauthorized access to sensitive information.

Cisco Security
AUGUST 24, 2023
Cisco is aware of reports that Akira ransomware threat actors have been targeting Cisco VPNs that are not configured for multi-factor authentication to infiltrate organizations, and we have observed instances where threat actors appear to be targeting organizations that do not configure multi-factor authentication for their VPN users.

Security Affairs
APRIL 28, 2024
From March 18, 2024, to April 16, 2024, Duo Security and Cisco Talos observed large-scale brute-force attacks against a variety of targets, including VPN services, web application authentication interfaces and SSH services.

Adam Levin
NOVEMBER 15, 2019
News that Virtual Private Network ( VPN ) provider NordVPN was breached spread quickly. While the breach of a major VPN service is newsworthy, this one wasn’t particularly. But one of the watchwords of good cyber hygiene, a VPN, was breached. Who Is Using VPNs? SMB vs. Enterprise.

Security Affairs
OCTOBER 21, 2023
Okta says that threat actors broke into its support case management system and stole authentication data, including cookies and session tokens, that can be abused in future attacks to impersonate valide users. HAR files can also contain sensitive data, including authentication information. ” concludes the advisory.

Security Affairs
NOVEMBER 24, 2024
CISA adds Apple, Oracle Agile PLM bugs to its Known Exploited Vulnerabilities catalog More than 2,000 Palo Alto Networks firewalls hacked exploiting recently patched zero-days Ransomhub ransomware gang claims the hack of Mexican government Legal Affairs Office US DoJ charges five alleged members of the Scattered Spider cybercrime gang Threat actor (..)

Security Boulevard
FEBRUARY 17, 2025
The more accounts you have, the bigger your attack surface and potential exposure to data breaches. Privacy Services Mullvad has partnered with Obscura VPN Mullvad Mullvad announces its partnership with ObscuraVPN; Mullvad WireGuard VPN servers can be used as the exit hop for the two-party VPN service offered by ObscuraVPN.

Thales Cloud Protection & Licensing
OCTOBER 28, 2021
Trick or Treat: The Choice is Yours with Multifactor Authentication. Whether you want the ‘trick’ of a malevolent threat actor infiltrating your network by exploiting a compromised password or the ‘treat’ from the peace of mind associated with multifactor authentication, the choice is yours. Fri, 10/29/2021 - 05:29.

Zero Day
JUNE 20, 2025
Here are the facts and how to protect yourself Wondering if your information is posted online from a data breach? PT Moor Studio/Getty With so much news about data breaches, you have to be careful not to panic each time you hear of a new one. Here's how to check if your accounts are at risk and what to do next.

Duo's Security Blog
DECEMBER 12, 2023
Certain risks may expose critical infrastructure to cyberattacks, enabling malicious actors to gain unauthorized access to critical business information and potentially causing large-scale data breaches. In fact, IBM's 2023 Cost of a Data Breach Report found that 82% of data breaches involved data stored in the cloud.

Security Affairs
JANUARY 13, 2024
” The ransomware attack reported in late 2023, targeted organizations’ networks using poorly secured VPN gateway on Cisco ASA or FTD devices. Rapid7 researchers, they noticed that threat activity targeting Cisco ASA SSL VPN appliances dates back to at least March 2023.

Security Affairs
JANUARY 13, 2024
Akira ransomware targets Finnish organizations GitLab fixed a critical zero-click account hijacking flaw Juniper Networks fixed a critical RCE bug in its firewalls and switches Vast Voter Data Leaks Cast Shadow Over Indonesia ’s 2024 Presidential Election Researchers created a PoC for Apache OFBiz flaw CVE-2023-51467 Team Liquid’s wiki leak exposes (..)

Webroot
OCTOBER 17, 2024
According to the Identity Theft Resource Center, there were 3,205 data compromises in 2023. A data compromise can consist of any of the following: Data breach : Unauthorized access to your confidential information (i.e. many of which resulted in consumer data exposure. That’s a 20% increase over the previous year.

Security Affairs
FEBRUARY 15, 2025
CISA adds Microsoft Windows, Zyxel device flaws to its Known Exploited Vulnerabilities catalog Microsoft Patch Tuesday security updates for February 2025 ficed 2 actively exploited bugs Hacking Attackers exploit a new zero-day to hijack Fortinet firewalls Security OpenSSL patched high-severity flaw CVE-2024-12797 Progress Software fixed multiple high-severity (..)

Duo's Security Blog
JUNE 2, 2021
This report Bridging Healthcare Security Gaps: Better Authentication Improves Controls aims to bring clarity and solutions to these security gaps. In this report you will learn: About zero trust and how multi-factor authentication meets the HIPPA requirements for a third factor of authentication.

Duo's Security Blog
FEBRUARY 16, 2022
Retail’s great “digital transformation” sped up, as did the number of data breaches impacting retail. The costs that follow a data breach are trending upward year over year. Data breach costs rose from $3.86 million, according to IBM and the Ponemon Institute’s Cost of Data Breach Report 2021.

Pen Test Partners
AUGUST 29, 2024
Multi-factor authentication (MFA) : MFA requires multiple forms of identification, adding an extra layer of security. Secure networks : Avoid using untrusted public Wi-Fi to access social media accounts, instead, use mobile data. You absolutely should secure your password manager with Multi-Factor Authentication (MFA).

Security Affairs
JANUARY 13, 2024
” The ransomware attack reported in late 2023, targeted organizations’ networks using poorly secured VPN gateway on Cisco ASA or FTD devices. Rapid7 researchers, they noticed that threat activity targeting Cisco ASA SSL VPN appliances dates back to at least March 2023.

CyberSecurity Insiders
APRIL 16, 2021
Organizations with weak cybersecurity have been severely punished with cyber-attacks, data breaches, and huge losses in the past. According to Varonis and RiskBased, over 4 billion records were illegally accessed through data breaches in 2019. Security through a VPN. Password managers and two-factor authentication.

Security Affairs
NOVEMBER 29, 2020
A cyberattack crippled the IT infrastructure of the City of Saint John Hundreds of female sports stars and celebrities have their naked photos and videos leaked online Romanians arrested for running underground malware services Threat actor shared a list of 49,577 IPs vulnerable Fortinet VPNs Computer Security and Data Privacy, the perfect alliance (..)

eSecurity Planet
SEPTEMBER 5, 2024
A VPN (Virtual Private Network) routes your internet traffic through an encrypted tunnel, shielding your data from hackers and ensuring your online activities remain private and secure. A VPN can provide the solution if you want to safeguard your personal information, bypass geo-restrictions, or maintain anonymity online.

Tech Republic Security
JULY 18, 2023
Use this comprehensive list of strategies to help you safeguard your company's data from threats and data breaches.

Identity IQ
JULY 8, 2024
RockYou2024: Nearly 10 Billion Passwords Exposed in Data Leak IdentityIQ In a cybersecurity incident that has sent shockwaves through the online community, nearly 10 billion unique passwords have been exposed in the “RockYou2024” data breach. billion passwords. The additional 1.5
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content