Researchers extract master encryption key from Siemens PLCs
CSO Magazine
OCTOBER 11, 2022
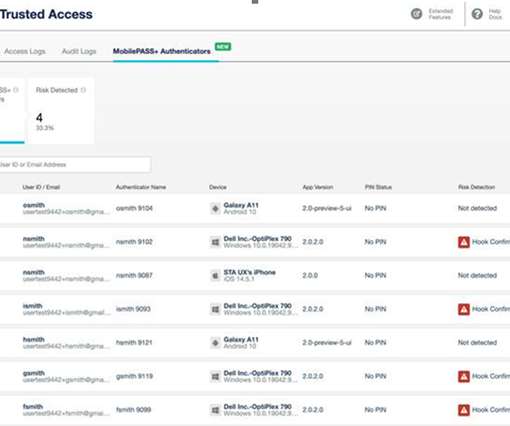
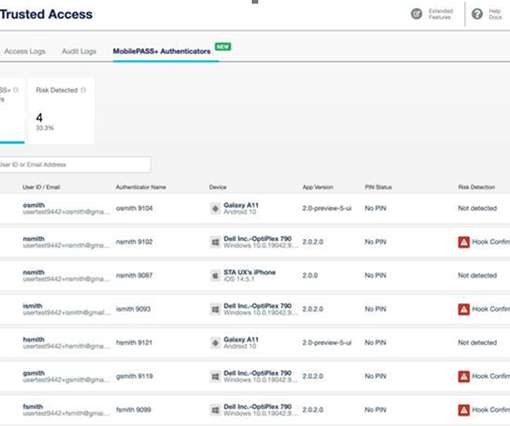
Security researchers have found a way to extract a global encryption key that was hardcoded in the CPUs of several Siemens programmable logic controller (PLC) product lines, allowing them to compromise their secure communications and authentication.













































Let's personalize your content