As 2-factor authentication falls short, ‘adaptive multi-factor authentication’ goes mainstream
The Last Watchdog
JUNE 28, 2018
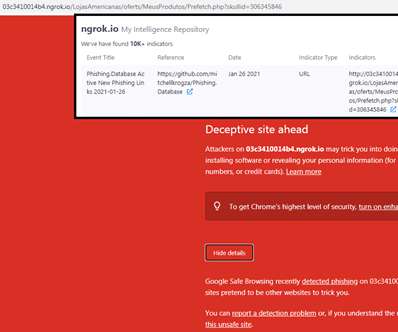
The use of an additional form of authentication to protect the accessing of a sensitive digital system has come a long way over the past decade and a half. An Israeli start-up, Silverfort , is seeking to make a great leap forward in the state-of-the-art of authentication systems. LW: Let’s come back to ‘adaptive authentication.’













































Let's personalize your content