VNC instances exposed to Internet pose critical infrastructures at risk
Security Affairs
AUGUST 15, 2022
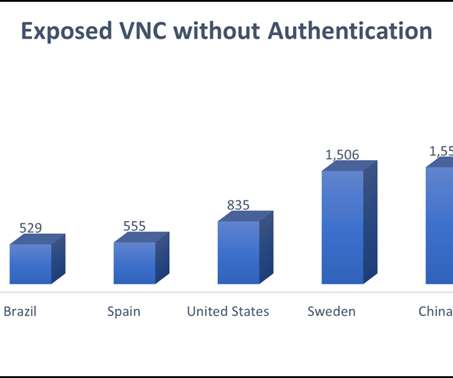
Researchers from Cyber looked for VNC exposed over the internet and discovered over 8000 VNC instances with authentication disabled, most of them in China, Sweden, and the United States. Exposing VNCs to the internet, increases the likelihood of a cyberattack. connected via VNC and exposed over the internet.












































Let's personalize your content