Hackers Claim They Breached T-Mobile More Than 100 Times in 2022
Krebs on Security
FEBRUARY 28, 2023
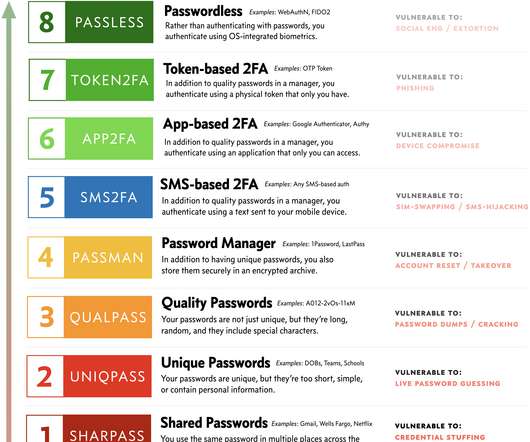
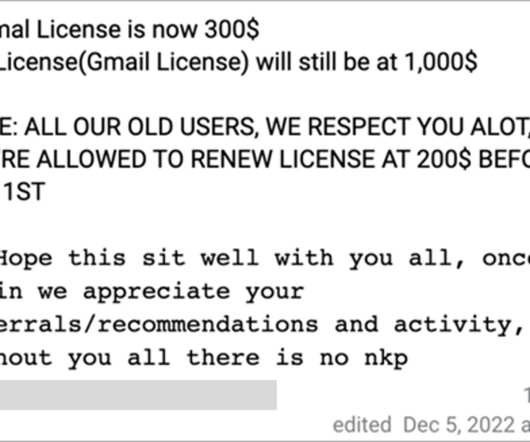
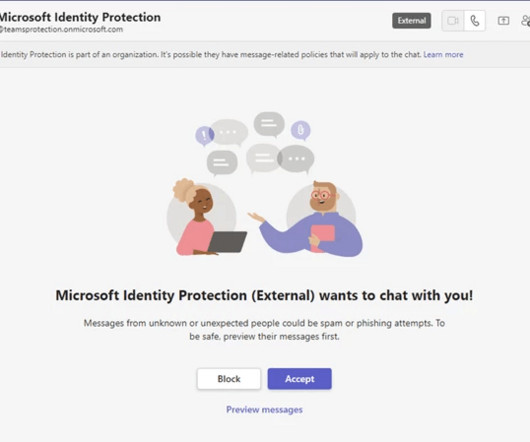
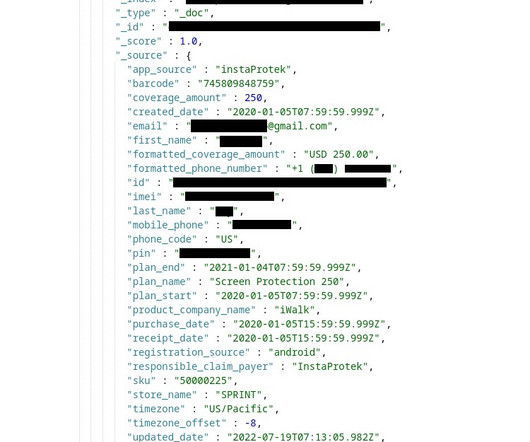
Image: Shutterstock.com Three different cybercriminal groups claimed access to internal networks at communications giant T-Mobile in more than 100 separate incidents throughout 2022, new data suggests. Countless websites and online services use SMS text messages for both password resets and multi-factor authentication.














































Let's personalize your content