ELFEN: Automated Linux Malware Analysis Sandbox
Penetration Testing
JANUARY 2, 2024
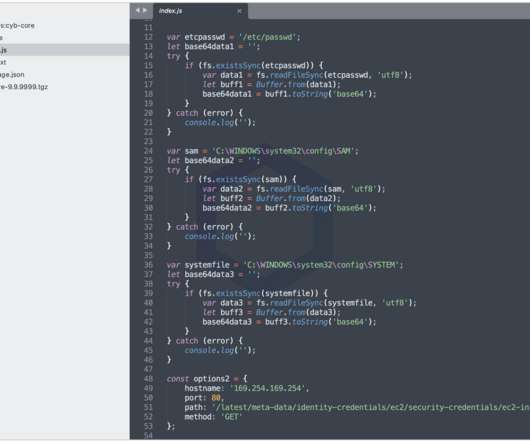
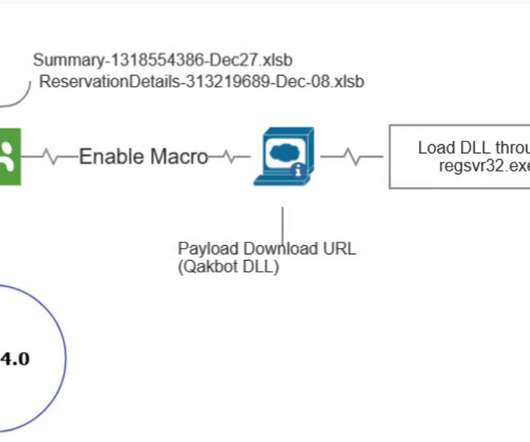
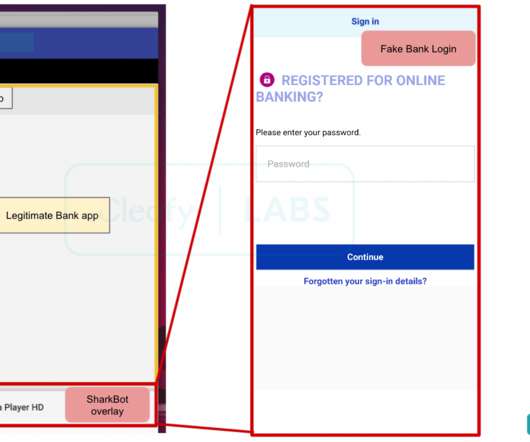
ELFEN: Linux Malware Analysis Sandbox ELFEN is a dockerized sandbox for analyzing Linux (file type: ELF) malware. It leverages an array of open-source technologies to perform both static and dynamic analysis.








































Let's personalize your content