Enhancing Cybersecurity Awareness: A Comprehensive Guide
CyberSecurity Insiders
JUNE 13, 2023
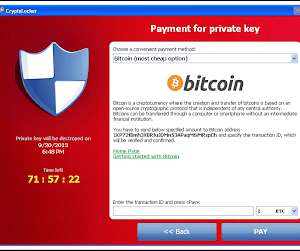
In our increasingly digital world, where technology permeates every aspect of our lives, cyber-security awareness has become an indispensable skill. This article will provide you with a comprehensive guide on how to create cybersecurity awareness and protect yourself and your digital assets from potential threats.




































Let's personalize your content