How to recover files encrypted by Yanlouwang
SecureList
APRIL 18, 2022
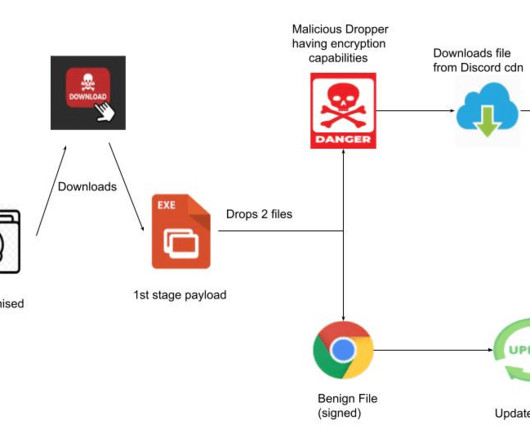
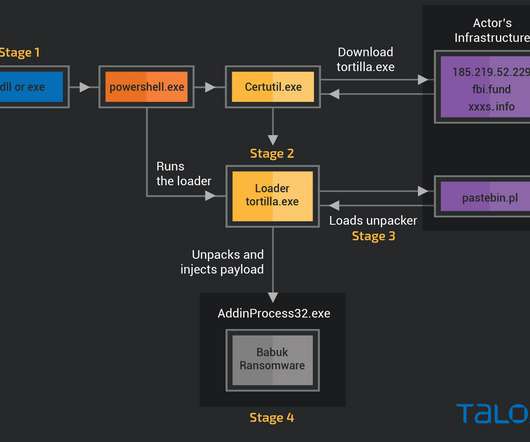
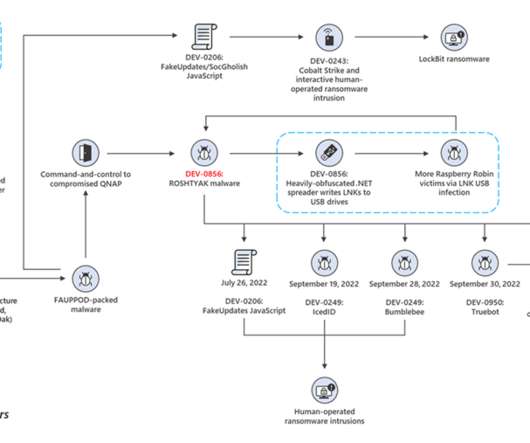
Kaspersky experts have found a vulnerability in the Yanluowang encryption algorithm and created a free decryptor to help victims of this ransomware with recovering their files. Geography of the Yanluowang attacks, December 4th, 2021 – April 8th, 2022 ( download ). The encryption code for big files. Yanluowang description.











































Let's personalize your content