Sophos blocked attacks exploiting XG Firewall zero-day to deploy Ransomware
Security Affairs
MAY 21, 2020
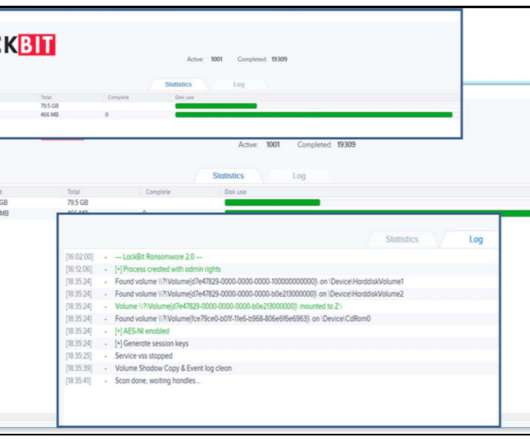
Hackers attempted to exploit a zero-day flaw in the Sophos XG firewall to distribute ransomware to Windows machines, but the attack was blocked. It was designed to download payloads intended to exfiltrate XG Firewall-resident data. Passwords associated with external authentication systems such as AD or LDAP are unaffected.
















































Let's personalize your content