Ukrainian Blackjack group used ICS malware Fuxnet against Russian targets
Security Affairs
APRIL 15, 2024
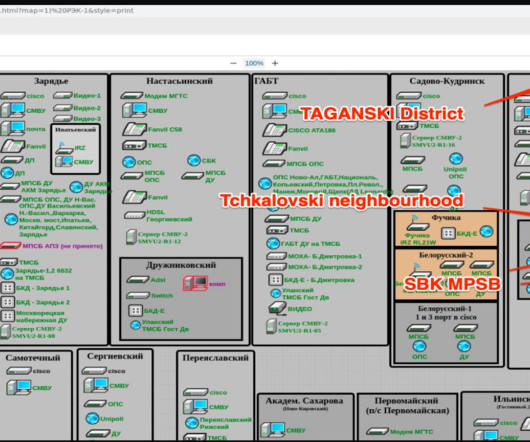
The website ruexfil.com provided detailed information about the attacks against Moscollector, the hackers also published screenshots of monitoring systems, servers, and databases they claim to have compromised. The site also hosts password dumps allegedly stolen from the Russian company. Access to 112 Emergency Service.
















































Let's personalize your content