Ukrainian Blackjack group used ICS malware Fuxnet against Russian targets
Security Affairs
APRIL 15, 2024
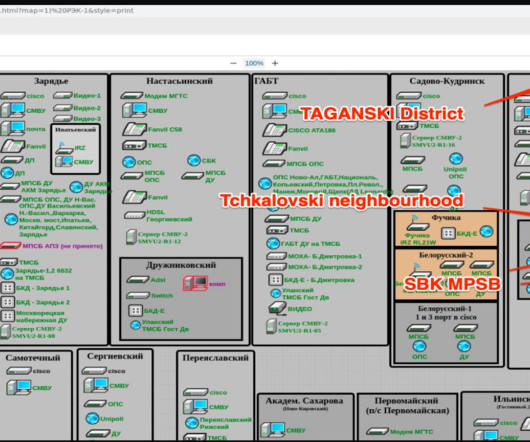
The Ukrainian hacking group Blackjack used a destructive ICS malware dubbed Fuxnet in attacks against Russian infrastructure. The Blackjack group is believed to be affiliated with Ukrainian intelligence services that carried out other attacks against Russian targets, including an internet provider and a military infrastructure.












































Let's personalize your content