CISA adds Veritas Backup Exec flaws to its Known Exploited Vulnerabilities catalog
Security Affairs
APRIL 8, 2023
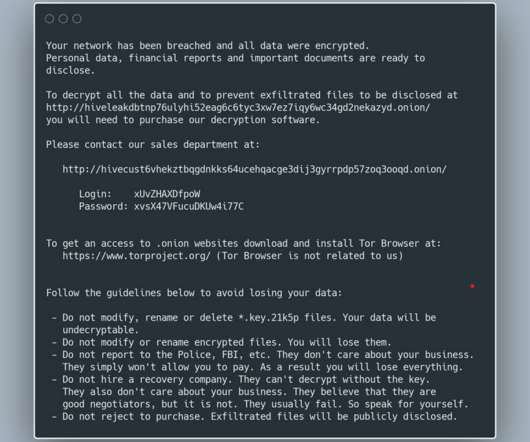
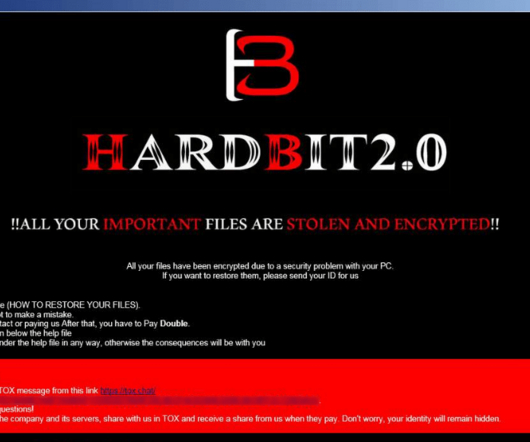
US CISA has added Veritas Backup Exec flaws, which were exploited in ransomware attacks, to its Known Exploited Vulnerabilities catalog. The CVE-2023-26083 flaw in the Arm Mali GPU driver is chained with other issues to install commercial spyware, as reported by Google’s Threat Analysis Group (TAG) in a recent report.





































Let's personalize your content