Ransomware Backup Strategy: Secure Your Backups
Spinone
FEBRUARY 5, 2020
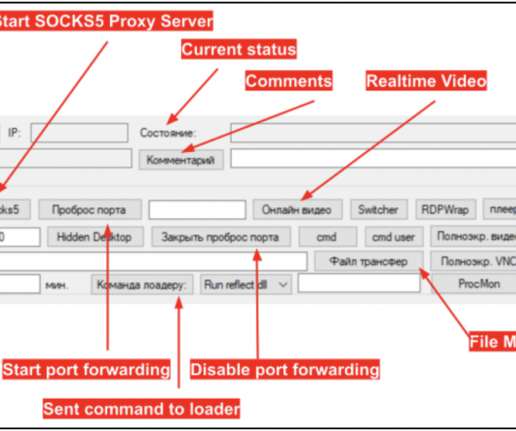
When someone asks you about the best ransomware protection , the first thing you’ll probably come up with is a backup. After all, backup is the only security practice that actually can get your infected data back. Ransomware can infect backups. Can Ransomware Encrypt Backups? But there is a problem.































Let's personalize your content