Forrester’s Top 10 Emerging Tech for 2025: Which 3 are Standouts?
Tech Republic Security
MAY 12, 2025
A Forrester VP explains to TechRepublic readers why three of these 10 emerging technologies for the year should be on managers' radar now.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
MAY 12, 2025
A Forrester VP explains to TechRepublic readers why three of these 10 emerging technologies for the year should be on managers' radar now.

The Last Watchdog
JANUARY 11, 2022
Last August, NTT , the Tokyo-based technology giant, unveiled its Health and Wellbeing initiative – an ambitious effort to guide corporate, political and community leaders onto a more enlightened path. and other jurisdictions have abjectly failed over the past 20 years leveraging Big Data to innovate personalized healthcare services.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
NOVEMBER 30, 2021
Indeed, APIs have opened new horizons of cloud services, mobile computing and IoT infrastructure, with much more to come. Masters reported that very little slowed him down as he discovered ways to make unauthenticated requests for private account data of Peloton cyclers including names, birth dates, gender, location, weight and workout stats.

The Last Watchdog
SEPTEMBER 27, 2021
Assessing the risks involved in using the latest technology is something our culture had to adopt in the early days of the computer. New technologies come with risks — there’s no denying that. Related: How Russia uses mobile apps to radicalize U.S. The Creeper Virus (1971). Lessons learned.

Security Affairs
DECEMBER 1, 2020
UK officials proposed to stop installing new Huawei equipment in the 5G network within the year, they also plan to speed up the replacement of Chinese technology that has been already deployed. The UK intelligence analysis believe that US ban on Chinese 5G technology will force Huawei to use untrusted technology.

Thales Cloud Protection & Licensing
JANUARY 31, 2018
As organizations continue to embrace digital transformation, greater amounts of sensitive data is created, stored and transferred in digital form putting more data at risk. Also with the increase in cloud, mobile, and IoT devices, a whole new generation of attack surfaces are vulnerable to hackers.
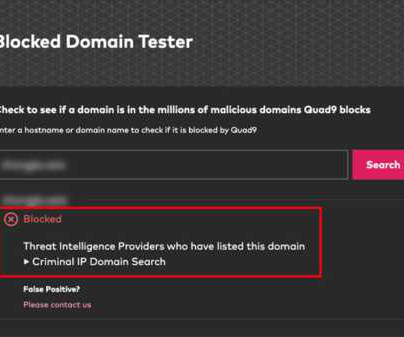
The Last Watchdog
MAY 13, 2024
May 13, 2024, CyberNewsWire — Criminal IP, a renowned Cyber Threat Intelligence (CTI) search engine developed by AI SPERA, has recently signed a technology partnership to exchange threat intelligence data based on domains and potentially on the IP address to protect users by blocking threats to end users. Torrance, Calif.,

CyberSecurity Insiders
JANUARY 11, 2022
The 2021 ISG Provider Lens Manufacturing Industry Services – Global report finds the complex mix of legacy OT and newer, connected technologies such as industrial IoT and machine learning has forced manufacturers to add security extensions for protection against cyberattacks.

eSecurity Planet
AUGUST 4, 2022
It’s been a couple of decades since data tapes delivered by trucks made encryption a standard enterprise cybersecurity practice. Yet even as technology has changed, sending and receiving data remains a major vulnerability, ensuring encryption’s place as a foundational security practice. What is Encryption?

Thales Cloud Protection & Licensing
MARCH 5, 2018
Healthcare’s IT evolution has brought numerous security challenges including regulations, the use of digitally transformative technologies that have created huge amounts of data to store and protect, and the extraordinary value of electronic personal health information (ePHI) to cybercriminals. Almost all (96%) of U.S.

Security Boulevard
FEBRUARY 24, 2021
Now, cybersecurity may just be the most important aspect of financial technology (fintech) in the modern world. With 2020 being the worst year on record in terms of files exposed in data breaches , a thorough security approach is necessary to combat modern dangers. Multi-cloud data storage. Regulatory technologies (Regtech). .

Thales Cloud Protection & Licensing
NOVEMBER 4, 2020
Companies and organizations, whether in the public or in the private sector, are re-establishing their business in the era of information and data revolution. businesses are taking advantage of digital technologies like cloud, mobile, and IoT to digitally transform their operations. Weak security practices lead to data breaches.

eSecurity Planet
APRIL 26, 2022
Company Sector Year Status Isovalent Cloud security 2020 Private Illumio Cloud security 2015 Private SignalFx Monitoring 2015 Acquired: Splunk CipherCloud Cloud security 2012 Acquired: Lookout Lookout Mobile security 2011 Private. Bessemer Venture Partners. Also read : Addressing Remote Desktop Attacks and Security. Evolution Equity Partners.

eSecurity Planet
JANUARY 27, 2022
Gartner analyst Pete Shoard advised that being as clear as possible about your needs is key to selecting the right service, noting that offerings can range from managing a single technology to sharing the responsibility for operating a security platform to full outsourcing of security operations. DXC Technology. Secureworks.

Thales Cloud Protection & Licensing
APRIL 23, 2018
Today, organizations are rapidly adopting cloud technology. 94 percent of respondents are using sensitive data in cloud, big data, IoT or mobile environments. But with widespread enterprise adoption of cloud technologies, come very real data security risks.

Thales Cloud Protection & Licensing
OCTOBER 18, 2018
While retailers digitally transform their businesses to better serve the higher demands of their customers, they’re being challenged with safeguarding personal data to protect customers, partners and suppliers’ critical information. retailers, especially, need to focus on data protection. The report shows that 95 percent of U.S.

CyberSecurity Insiders
MAY 22, 2021
the flash memory affiliate of Kingston Technology Company, Inc., the flash memory affiliate of Kingston Technology Company, Inc., Wireless, Mobile, or Portable Device Security — Most Innovative. Kingston and the Kingston logo are registered trademarks of Kingston Technology Corporation. FOUNTAIN VALLEY, Calif.–(

Thales Cloud Protection & Licensing
FEBRUARY 28, 2022
To enable this revolution, automobile manufacturers and their supply chain partners have rapidly adopted new technologies to better serve customers and win competitive advantages: Embedding high-speed connectivity in vehicles to improve customer experience and entertainment as well as real-time diagnostics and OTA updates.

Thales Cloud Protection & Licensing
DECEMBER 5, 2018
Two other key drivers are digital transformation and poor investments in IT security tools needed to protect data. With digital transformation technologies like cloud, big data, IoT, containers, mobile payments and blockchain all in play, there are many new attack surfaces and risks to financial data.

Security Boulevard
FEBRUARY 23, 2022
As a trusted cybersecurity specialist, the company helps to drive the transition to a totally trusted digital world, powered by a best-in-class technology portfolio and together we are looking forward to taking those partners and their end customers on their journey to achieve best in class API security.

eSecurity Planet
JUNE 24, 2021
The increasing mobility of data, as it ping-pongs between clouds, data centers and the edge, has made it an easier target of cybercrime groups, which has put a premium on the encryption of that data in recent years. Dirk Schrader, global vice president of security research at New Net Technologies, agreed.

Thales Cloud Protection & Licensing
MARCH 1, 2019
The report shows that 97% of enterprises adopting digital transformation technologies use sensitive data within these new environments, but only 30% use encryption to protect data in these environments. Enterprises must focus on the protection of the sensitive data itself, wherever it goes.

SecureWorld News
JULY 28, 2020
How do technology leaders view remote work and cybersecurity? In contrast, only 30% of employees say their employer offered training on the dos and don'ts of protecting company and personal digital assets, data and information.". And other portions of the survey reveal pain points around the endpoint and big data.

Security Boulevard
AUGUST 17, 2021
With the advancements in technology every year, the need for protection against cyber threats increases as well. Stronger technologies mean hackers and cyber attackers have better weapons to hit us with. Those industries need the latest and up-to-date cybersecurity practices to keep their data safe.

CyberSecurity Insiders
JANUARY 17, 2022
The SCA demonstrates a committed investment in cloud technology that will enable partners to expand their offerings to reach larger markets. ” “TD SYNNEX has been a great partner for us in enabling us to effectively build and scale our AWS practice,” said John Zemonek, Managing Partner of Aligned Technology Group.

Thales Cloud Protection & Licensing
JUNE 14, 2018
Luckily, zebras don’t use mobile devices, or manufacturers would be hard at work on stripe recognition technology. I invite you to read Juan’s blog to learn more about the challenges and approaches to protecting the big data behind the analytics. For more information about Entrust, please visit our partner page.

CyberSecurity Insiders
JANUARY 4, 2022
The partnership expands the TD SYNNEX IoT, data, and analytics portfolio of partners to include a comprehensive software platform for self-service data discovery, enterprise reporting, mobile applications, and embedded analytics. “We Learn more at microstrategy.com.

Thales Cloud Protection & Licensing
OCTOBER 23, 2019
DX technologies such as cloud, mobile payments, IoT, Big Data and others have fundamentally changed retailers’ business models, not only by opening new channels to reach customers, but also in how they communicate with, serve, and support them. Encryption technologies are the top tools needed.

McAfee
JUNE 12, 2020
As most of us are aware, digital transformation through big data analytics, online transactions, the Internet of Things (IoT) and cloud-based applications has dramatically changed businesses of all kinds. At the same time, workers have become mobile on a global scale, requiring access to ever larger amounts of data.

eSecurity Planet
AUGUST 22, 2023
Enter flow technologies such as NetFlow, which deliver performance metrics while providing over 90 percent of the visibility available from packet analysis. NetFlow collection systems manage packet data so security teams can study it as needed, determining where a breach is most likely to happen.

Pen Test
OCTOBER 12, 2023
The rapid advancement of technology has woven a complex fabric of wireless networks, each interwoven with vulnerabilities waiting to be exposed. It underscores the vital role it plays in fortifying the burgeoning landscape of wireless technologies. Radio Frequency (RF) stands as a pivotal component in today's technological landscape.

CyberSecurity Insiders
OCTOBER 1, 2021
. “We are fortunate to have a key partner in Cohesity who recognizes the value our combined efforts bring to the technology ecosystem,” said Michael Urban, president of Americas, TD SYNNEX. We’re committed to uniting IT solutions that deliver business outcomes for customers today and unlock growth for the future.

SecureWorld News
APRIL 3, 2023
The origins of Security Data Lake The idea of a Security Data Lake ( SDL) is rooted in the traditional idea of a Data Lake. Its inception was driven by the exponential growth of data and declining storage costs. A Data Lake is a storage repository that keeps vast amounts of data in its original format.

Privacy and Cybersecurity Law
SEPTEMBER 21, 2017
Consent and Technology. In 2016, the OPC issued a consultation paper regarding the challenges of obtaining meaningful consent in a continuously evolving technological ecosystem where the traditional “privacy policy” may not always be suitable. and Europe. issuing binding orders, and. impose administrative monetary penalties.

eSecurity Planet
AUGUST 15, 2022
Security Information and Event Management (SIEM) is a crucial enterprise technology that ties the stack of cybersecurity systems together to assess threats and manage risks. A screenshot of the MVISION Mobile dashboard on the Trellix SIEM platform. Unified storage of logs capable of big-data searches and visualizing analytics.

Thales Cloud Protection & Licensing
JUNE 6, 2018
Gartner defines digital risk management as “the integrated management of risks associated with digital business components, such as cloud, mobile, social, big data, third-party technology providers, OT and the IoT.” As Technology Evolves New Vulnerabilities Arise. Interested in learning more?

McAfee
JUNE 29, 2020
However, enterprises nowadays require an extended protective umbrella that can defend not just legacy endpoints, but also mobile, and cloud workloads – all without overburdening in-house staff or requiring even more resources. Detecting today’s advanced threats requires more than a collection of point solutions.

Spinone
JANUARY 21, 2018
With the technologies in cloud computing moving so fast, and adoption rates increasing rapidly, we can expect to see some exciting developments in 2017. There has been criticism in recent years about the energy requirements of massive data centres and how adopting cloud technology may not be as green as it first seems.

Spinone
DECEMBER 26, 2018
The contemporary world has witnessed the rise of the Internet and global communication, and collaboration technologies, including mobile data use and the culture of bring your own device [BYOD].

NopSec
JANUARY 2, 2014
One of the big concerns is accidental disclosure due to information being held in an unprotected manner on consumer devices. Due to the inherently less secure configurations of personal devices and increasingly sophisticated mobile malware, external manipulation of software vulnerabilities is a real threat.

Security Boulevard
JANUARY 26, 2024
There is a Very Large and Serious Customer Problem to be Solved One of the things that was surprising to me was just how big the API security problem is. Since you can’t really see an API, like you might see a laptop or mobile phone, it’s easy to forget about it. But the number of APIs in the world continues to grow, and grow rapidly.

CyberSecurity Insiders
JUNE 11, 2021
Sustainability – Applying AI, machine learning, and advanced analytics to support sustainability initiatives for energy consumption and greenhouse gas emissions: Learning in Routing Games for Sustainable Electromobility (Henrik Sandberg, KTH Royal Institute of Technology). Wei Liu, KTH Royal Institute of Technology). The ten C3.ai

eSecurity Planet
JANUARY 21, 2021
Mobile app? LogicManager’s GRC solution has specific use cases across financial services, education, government, healthcare, retail, and technology industries, among others. Like other competitive GRC solutions, it speeds the process of aggregating and mining data, building reports, and managing files. Fusion Framework GRC.

Spinone
NOVEMBER 15, 2016
Information Technology research and advisory company, Gartner, presented its top predictions for the cybersecurity industry for 2017 earlier this year. The entire cybersecurity strategy for any organization must be reviewed and updated regularly in order to keep up with new risks and technologies.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content