Top Trending CVEs of May 2023
NopSec
MAY 31, 2023
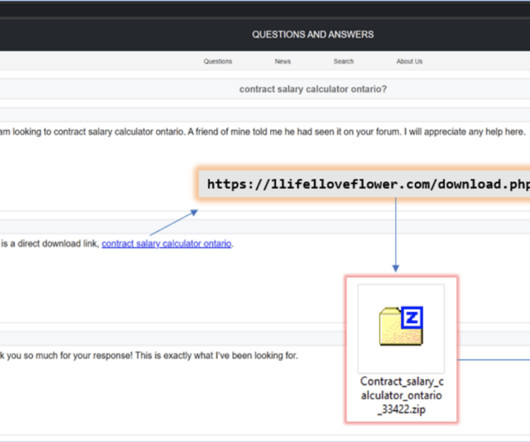
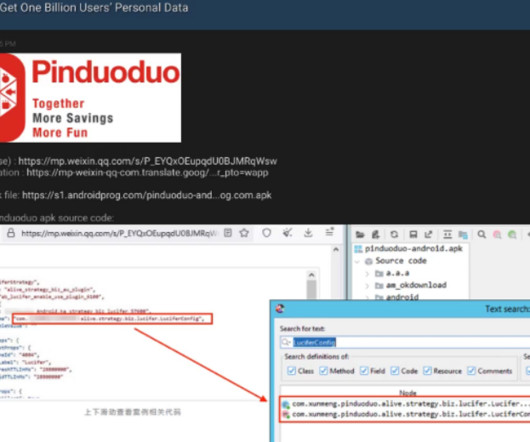
May was a rather quiet month for security research, but an excellent write up filtered to the masses from the Pwn2own 2023 conference held in Vancouver, B.C. Finally, it wouldn’t be a worthy blog post if we didn’t include a nugget from patch Tuesday. tar file manipulation. tar file manipulation. x) and VMware Fusion (13.x)

















Let's personalize your content