PACMAN, a new attack technique against Apple M1 CPUs
Security Affairs
JUNE 11, 2022
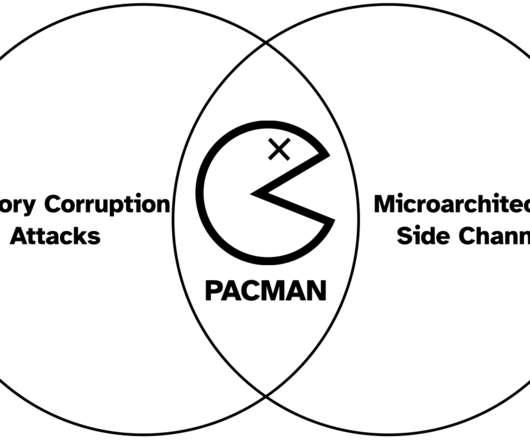
We present PACMAN, a novel attack methodology that speculatively leaks PAC verification results via micro-architectural side channels without causing any crashes.” The key insight of our PACMAN attack is to use speculative execution to stealthily leak PAC verification results via microarchitectural side channels.”






























Let's personalize your content